In an era defined by digital connectivity, ensuring the security of our online presence has become paramount. As we navigate the vast landscape of the internet, understanding the intricacies of online security is no longer a choice—it’s a necessity. This article serves as a comprehensive introduction, shedding light on the importance, risks, and fundamental practices associated with online security.
Table of Contents
ToggleTable of contents
What is online security?
Online security is a multifaceted discipline aimed at protecting digital information and assets from unauthorized access and cyber threats. It encompasses a range of strategies, technologies, and best practices designed to ensure the confidentiality, integrity, and availability of data in the digital realm. Common types of online security include encryption, which involves encoding data to prevent unauthorized access; firewalls, which serve as a barrier between a trusted internal network and untrusted external networks; antivirus software, designed to detect and remove malicious software; multi-factor authentication, requiring users to provide multiple forms of identification; secure browsing practices, emphasizing caution while navigating websites; and regular software updates, ensuring that systems have the latest security patches to defend against vulnerabilities. Implementing a combination of these measures is crucial for individuals and organizations to establish a robust defense against the ever-evolving landscape of online threats.
Types of Online Security
1. Encryption:
Encryption involves encoding data to make it unreadable without the correct decryption key. It protects sensitive information during transmission and storage, ensuring that even if intercepted, the data remains secure.
2. Firewalls:
Firewalls act as a protective barrier between a trusted internal network and untrusted external networks, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules.
3. Antivirus Software:
Antivirus software is designed to detect, prevent, and remove malicious software (malware) such as viruses, worms, and Trojan horses. It regularly scans systems to identify and neutralize potential threats.
4. Multi-Factor Authentication (MFA):
MFA adds an extra layer of security by requiring users to provide multiple forms of identification before accessing a system or account. This typically involves a combination of passwords, security tokens, or biometric authentication.
5. Secure Browsing Practices:
Secure browsing involves adopting safe habits while navigating the internet, such as avoiding suspicious websites, verifying the legitimacy of links, and using HTTPS connections to encrypt data during online interactions.
6. Regular Software Updates:
Keeping software up-to-date is crucial for security. Regular updates, often including security patches, help fix vulnerabilities in software that could be exploited by cyber attackers.
7. Intrusion Detection Systems (IDS):
IDS monitors network or system activities for malicious actions or security policy violations. They generate alerts or take predefined actions when potential threats are detected.
8. Virtual Private Networks (VPNs):
VPNs create a secure, encrypted connection over the internet, allowing users to browse privately and securely. They are commonly used to protect data when accessing public Wi-Fi networks.
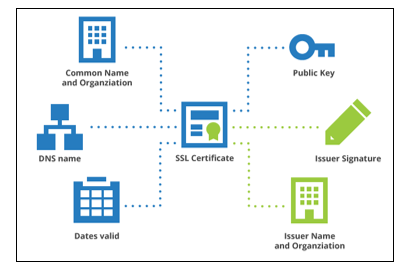
9. Security Certificates (SSL/TLS):
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) protocols provide a secure channel over the internet by encrypting data between a user’s browser and a website, ensuring the integrity of transmitted information.
10. Access Control Systems:
Access control systems manage user permissions and restrict access to sensitive data or areas of a network. This helps prevent unauthorized individuals from gaining entry to critical systems.
11. Backup and Recovery Systems:
Regular data backups and robust recovery plans are essential for minimizing data loss in the event of a security incident. These measures enable the restoration of systems and data to a previous state.
12. User Education and Awareness:
Educating users about potential online threats and promoting awareness of security best practices is crucial. Informed users are better equipped to recognize and avoid potential risks.
The Growing Importance of Online Security
In recent years, the importance of online security has grown exponentially. As we embrace the convenience of digital interactions, safeguarding personal information becomes a critical aspect of our daily lives. This section explores the factors contributing to the increasing relevance of online security and why it matters more than ever.
Why Online Security Matters
Online security matters for a variety of reasons, given the pervasive nature of digital interactions in our daily lives. Here are several key reasons why online security is of paramount importance:
1. Protection of Personal Information:
Online security safeguards sensitive personal information, such as names, addresses, and financial details, preventing unauthorized access and potential misuse by malicious actors.
2. Financial Security:
Ensuring online security is crucial for protecting financial assets. It prevents unauthorized access to bank accounts, credit cards, and other financial accounts, reducing the risk of fraud and financial loss.
3. Prevention of Identity Theft:
Robust online security measures help prevent identity theft, where cybercriminals steal personal information to impersonate individuals for fraudulent activities.
4. Confidentiality of Communication:
Online security measures, such as encryption, maintain the confidentiality of digital communications, ensuring that sensitive information shared over networks remains private and secure.
5. Safeguarding Business Data:
For businesses, online security is essential to protect proprietary information, trade secrets, and client data. Breaches can have severe financial and reputational consequences.
6. Mitigation of Cyber Attacks:
Online security measures are the frontline defense against various cyber attacks, including malware, phishing, and ransomware, minimizing the risk of data breaches and disruptions to services.
7. Preservation of Privacy:
Online security helps preserve individuals’ privacy by safeguarding personal data from unwarranted surveillance or unauthorized collection by companies, advertisers, or governments.
8. Preventing Online Harassment and Cyberbullying:
Effective online security measures contribute to the prevention of online harassment and cyberbullying, protecting individuals from malicious attacks and digital abuse.
9. Maintaining Trust in Digital Transactions:
Trust is fundamental in online transactions. Strong security measures, such as secure payment gateways and encrypted connections, foster confidence among users engaging in digital transactions.
10 National Security Concerns:
Cybersecurity is critical for national security, as cyber-attacks can target critical infrastructure, government systems, and sensitive military information, posing a threat to the security of nations.
11. Preservation of Reputation:
Individuals and businesses alike rely on a positive online reputation. A security breach can lead to data leaks, damaging the trust and reputation built over time.
12. Ensuring Business Continuity:
Online security contributes to business continuity by minimizing the impact of security incidents. Robust security measures help organizations recover quickly and resume normal operations after an attack.
13. Protection Against Exploitation of Vulnerabilities:
Regular updates and patches, part of online security practices, protect against the exploitation of software vulnerabilities by cybercriminals seeking unauthorized access to systems.
14. Compliance with Regulations:
Many industries have regulatory requirements mandating specific security standards. Compliance ensures that organizations adhere to these standards, avoiding legal consequences and penalties.
15. Global Connectivity:
In an interconnected world, online security is essential for maintaining global trust and cooperation. Individuals and businesses must ensure the security of their online interactions to foster a safer digital environment.
The significance of online security extends far beyond individual concerns, impacting societal, economic, and geopolitical realms. By recognizing and addressing the importance of online security, individuals and organizations can contribute to a safer and more resilient digital landscape.
Your Digital Footprint
A digital footprint refers to the trail of data created by an individual’s online activities. It encompasses everything a person does online, including social media interactions, website visits, online purchases, and even the use of connected devices. This digital trail is persistent and can have far-reaching implications, shaping how others perceive and interact with an individual in the digital realm.
Every click, like, and share adds to this digital footprint, creating a comprehensive profile of a person’s online behavior. The concept is especially relevant in an era where our lives are increasingly intertwined with digital platforms. Here’s an examination of the concept of a digital footprint and the implications of having an extensive digital presence:
**Permanent Record:
A digital footprint is akin to a permanent record of one’s online activities. Even seemingly innocuous actions, such as liking a post or commenting on a photo, contribute to this record. Over time, this accumulation of data paints a detailed picture of a person’s interests, preferences, and interactions.
**Online Reputation:
An extensive digital presence directly influences an individual’s online reputation. Employers, colleagues, friends, and potential connections often turn to online platforms to gather information about a person. A positive digital footprint can enhance professional opportunities and personal relationships, while a negative one can have detrimental effects.
**Privacy Concerns:
The more extensive the digital footprint, the greater the potential for privacy concerns. Information shared online can be collected, aggregated, and analyzed by various entities, leading to the risk of personal data being misused, hacked, or sold without the individual’s consent.
**Targeted Advertising:
Online platforms use digital footprints to tailor advertisements based on user preferences and behaviors. While this can enhance the user experience, it also raises concerns about data manipulation and the potential exploitation of personal information for financial gain.
**Identity Theft and Fraud:
A comprehensive digital footprint may expose individuals to the risk of identity theft and fraud. Malicious actors can exploit the information available online to impersonate someone, gain unauthorized access to accounts, and financial data, or even commit criminal activities under the victim’s identity.
**Social Engineering Attacks:
An extensive digital presence provides cybercriminals with valuable information for social engineering attacks. By exploiting details gathered from the digital footprint, attackers can craft convincing phishing emails or messages to manipulate individuals into divulging sensitive information.
**Impact on Offline Life:
The implications of a digital footprint extend beyond the online world. Information discovered online can influence real-world decisions, affecting employment opportunities, social relationships, and even legal matters.
**Digital Legacy:
The digital footprint persists even after an individual has passed away. Managing one’s digital legacy becomes crucial, as the information left behind can impact how loved ones remember and interact with the person posthumously.
**Data Brokerage and Profiling:
Companies involved in data brokerage often buy and sell information derived from digital footprints. This profiling can lead to the creation of detailed consumer profiles, raising concerns about the commodification of personal data.
**Educational and Institutional Impact:
Educational institutions and employers may scrutinize digital footprints during admissions or hiring processes. Unfavorable online behavior or content could have consequences for academic and professional opportunities.
In conclusion, individuals need to be aware of the lasting impressions their online activities leave through their digital footprints. Proactive management of one’s digital presence, careful consideration of privacy settings, and mindful engagement in online spaces are essential practices to navigate the digital landscape responsibly and protect against potential risks.
Common Online Threats
Navigating the online world effectively requires a keen awareness of common threats that can compromise your digital security. Here’s an overview of prevalent online threats and insights into how they can pose risks to your digital security:
- Malware:
- Overview: Malware, short for malicious software, encompasses a variety of harmful programs designed to disrupt, damage, or gain unauthorized access to computer systems. This includes viruses, worms, trojan horses, ransomware, and spyware.
- Compromise: Malware can be distributed through infected websites, email attachments, or compromised software. Once on a device, it can steal sensitive information, damage files, or grant unauthorized access to cybercriminals.
- Phishing:
- Overview: Phishing is a deceptive tactic where attackers impersonate trustworthy entities to trick individuals into providing sensitive information such as passwords, credit card details, or login credentials.
- Compromise: Phishing attacks often come in the form of fraudulent emails, messages, or websites that appear legitimate. Clicking on malicious links or disclosing information in response to these deceptive communications can lead to identity theft or unauthorized access.
- Social Engineering:
- Overview: Social engineering involves manipulating individuals into divulging confidential information or performing actions that compromise security. This can include psychological manipulation, impersonation, or exploiting trust.
- Compromise: Attackers may use social engineering to trick individuals into revealing passwords, clicking on malicious links, or providing access to secure systems. This tactic relies on exploiting human psychology rather than technical vulnerabilities.
- Ransomware:
- Overview: Ransomware is a type of malware that encrypts a user’s files or entire system, demanding a ransom payment for their release. It can lead to data loss, financial extortion, and disruption of operations.
- Compromise: Ransomware is often spread through phishing emails or malicious downloads. Once activated, it encrypts files, rendering them inaccessible until a ransom is paid, though payment does not guarantee the return of data.
- Man-in-the-Middle Attacks:
- Overview: In a man-in-the-middle (MitM) attack, an attacker intercepts and potentially alters communication between two parties without their knowledge. This can occur in various online interactions, including email, messaging, or online transactions.
- Compromise: MitM attackers can eavesdrop on sensitive information, modify communications, or inject malicious content. This can lead to unauthorized access, data theft, or the interception of confidential information.
- Credential Stuffing:
- Overview: Credential stuffing is an attack where cybercriminals use stolen username and password combinations from one service to gain unauthorized access to other accounts, exploiting individuals who reuse passwords.
- Compromise: If individuals use the same login credentials across multiple platforms, a security breach on one site can lead to unauthorized access to other accounts. Cybercriminals often employ automated tools to test stolen credentials on various services.
- Cross-Site Scripting (XSS):
- Overview: XSS attacks involve injecting malicious scripts into web pages viewed by others. These scripts can execute in the browsers of unsuspecting users, leading to the theft of cookies, session data, or other sensitive information.
- Compromise: XSS vulnerabilities can be exploited to compromise user data, session hijacking, or defacement of websites. Attackers typically embed malicious scripts in input fields or URLs that are later executed by other users’ browsers.
- Zero-Day Exploits:
- Overview: Zero-day exploits target vulnerabilities in software or hardware that are unknown to the vendor. Attackers exploit these vulnerabilities before a patch or fix is developed, making it challenging for users to defend against such attacks.
- Compromise: Zero-day exploits can result in unauthorized access, data breaches, or the deployment of malware. Because users are unaware of the vulnerabilities, preventative measures are limited until the vendor releases a patch.
To enhance your digital security, it’s essential to stay informed about these threats, adopt proactive cybersecurity practices, regularly update software and applications, use strong and unique passwords, and exercise caution when interacting online. Employing a combination of security measures can significantly reduce the risk of falling victim to these common online threats.
The Evolving Landscape of Cybersecurity
The history of cybersecurity is a dynamic narrative shaped by the continuous evolution of technology and the ever-changing tactics of cyber threats. Here’s a brief journey through key milestones in the history of cybersecurity:
- 1970s – Birth of Computer Security:
- The concept of computer security emerged in the early days of computing. In the 1970s, pioneers like James Anderson and Willis Ware laid the groundwork for securing computer systems, focusing on access controls and protection mechanisms.
- 1980s – Rise of Malware:
- The 1980s saw the emergence of the first notable malware. The Elk Cloner, a boot sector virus affecting Apple II computers, marked an early instance of malicious software. This decade also witnessed the advent of early antivirus programs.
- 1990s – Internet Expansion and Worms:
- The widespread adoption of the internet in the 1990s brought new cybersecurity challenges. The Morris Worm in 1988 was one of the first internet-wide incidents, highlighting the potential for self-replicating code to disrupt systems. This era also saw the commercialization of antivirus solutions.
- 2000s – Rise of Cybercrime and Advanced Persistent Threats (APTs):
- The 2000s witnessed a surge in cybercrime activities, with the rise of worms, viruses, and financially motivated attacks. Notable incidents included the ILOVEYOU worm and the emergence of sophisticated APTs, targeting governments and corporations.
- 2010s – Proliferation of Ransomware and Nation-State Attacks:
- Ransomware became a prominent threat in the 2010s, with attacks like CryptoLocker encrypting user files and demanding payments for decryption keys. Nation-state-sponsored attacks, such as Stuxnet, demonstrated the potential for cyber-espionage and sabotage.
- 2020s – Supply Chain Attacks and IoT Vulnerabilities:
- The 2020s brought new challenges, including supply chain attacks like the SolarWinds incident, where malicious actors compromised a widely used software update. Vulnerabilities in Internet of Things (IoT) devices became a growing concern, leading to increased attention on securing interconnected devices.
- Current Landscape – Cloud Security and AI Integration:
- The current cybersecurity landscape is characterized by the widespread adoption of cloud services, introducing new considerations for securing data stored in remote servers. Integration of artificial intelligence and machine learning is enhancing threat detection capabilities and response times.
Key Themes Illustrating the Dynamic Nature of Cybersecurity:
- Adaptive Threat Landscape:
- Cyber threats continually evolve to exploit emerging technologies and vulnerabilities. Threat actors adapt their tactics, techniques, and procedures (TTPs) to bypass traditional security measures.
- Increasing Sophistication of Attacks:
- Cyberattacks have become more sophisticated over time, with nation-states, organized crime groups, and individual hackers employing advanced techniques. The development of APTs and targeted attacks demonstrates a higher level of planning and sophistication.
- Expanding Attack Surface:
- As technology advances, the attack surface expands. The proliferation of connected devices, IoT, and cloud services introduces new entry points for cyber threats, requiring a broader and more complex approach to cybersecurity.
- Collaborative Defense Strategies:
- The interconnected nature of cyberspace has led to increased collaboration among organizations, governments, and cybersecurity professionals. Sharing threat intelligence, best practices, and coordinated responses are essential components of modern cybersecurity defenses.
- Shift to Zero Trust Security:
- Traditional security models based on perimeter defenses are giving way to a Zero Trust approach, where trust is never assumed, and continuous verification is required for all users and devices, regardless of their location.
- Emphasis on Human-Centric Security:
- Recognizing the role of human factors in cybersecurity, there’s an increased emphasis on user education, awareness, and training. Social engineering attacks, such as phishing, highlight the importance of addressing the human element in security.
The history of cybersecurity underscores the necessity for a dynamic and adaptive approach to counter evolving threats. As technology continues to progress, the field of cybersecurity will remain at the forefront of safeguarding digital assets and maintaining the integrity of the digital realm.
Personal and Financial Risks
Understanding the specific risks associated with personal and financial information is essential. Real-world examples of security breaches leading to financial loss underscore the importance of safeguarding sensitive data.
Privacy Concerns in the Digital Age
In the digital age, the erosion of privacy has become an undeniable reality, driven by the pervasive integration of technology into our daily lives. The convenience offered by digital services often comes at the cost of personal privacy, prompting a crucial reflection on the delicate balance between the two.
1. Data Collection and Profiling:
- The convenience of online services and applications frequently requires users to share personal information. From social media platforms to e-commerce websites, user data is collected and often used to create detailed profiles. This extensive profiling enables targeted advertising and personalized recommendations but raises concerns about the extent of data that companies possess about individuals.
2. Internet of Things (IoT) and Smart Devices:
- The proliferation of IoT devices and smart technologies in homes contributes to the erosion of privacy. Smart speakers, thermostats, and cameras collect data on daily activities, creating a detailed picture of individuals’ lives. While these devices offer convenience, they also raise concerns about the security and privacy implications of constant data monitoring.
3. Location Tracking and Geotagging:
- Mobile devices, equipped with GPS technology, constantly track users’ locations. This information is used for mapping services, location-based recommendations, and targeted advertising. While location tracking can enhance convenience, it also poses significant privacy risks, as individuals’ movements are continuously monitored and recorded.
4. Social Media Sharing and Surveillance:
- The popularity of social media platforms has led to a culture of sharing personal experiences, thoughts, and photos. However, the constant sharing of information on these platforms raises privacy concerns. Moreover, the algorithms powering social media contribute to a surveillance-like environment, where user behavior is closely monitored for advertising purposes.
5. Surveillance Capitalism:
- The business model of many tech companies relies on the monetization of user data, a concept known as surveillance capitalism. Personal information is commodified, leading to an erosion of privacy as individuals become products, and their online activities are exploited for profit.
6. Biometric Data and Facial Recognition:
- The convenience of unlocking devices or accessing services using biometric data, such as fingerprints or facial recognition, has become commonplace. However, the collection and use of biometric information pose significant privacy risks, especially when used in mass surveillance or for purposes beyond initial user consent.
7. Privacy Policies and Consent Challenges:
- The lengthy and often complex privacy policies that users must agree to when using online services contribute to the erosion of privacy. Users may unknowingly consent to extensive data collection and sharing, highlighting the challenge of obtaining informed consent in the digital age.
8. Cybersecurity Threats and Data Breaches:
- The interconnected world is susceptible to cybersecurity threats and data breaches. Personal information, once entrusted to online platforms, may be exposed in large-scale breaches, compromising individuals’ privacy. The convenience of digital services is overshadowed by the potential risks associated with the loss of sensitive data.
In navigating this landscape, individuals must recognize the trade-offs between convenience and privacy. While the digital age offers unprecedented ease of access and personalized experiences, it is essential to critically assess the extent to which personal information is shared and the potential consequences of doing so. Striking a balance between enjoying the benefits of technology and safeguarding one’s privacy requires informed decision-making, advocacy for transparent data practices, and a collective push for ethical standards in the digital realm. Ultimately, the erosion of privacy in the interconnected world prompts us to consider the implications of sacrificing this fundamental right in the pursuit of convenience.
Introduction to Cybercrime
Cybercrime Definition:
Cybercrime refers to criminal activities carried out using digital technologies, computer networks, and the internet. These illicit activities exploit vulnerabilities in technology to compromise data, steal sensitive information, commit fraud, or disrupt digital systems. Cybercriminals employ various techniques to exploit cybersecurity weaknesses, and the range of cybercrimes continues to evolve as technology advances.
Manifestations of Cybercrime:
Cybercrime manifests in various forms, each posing distinct threats to individuals, businesses, and governments:
- Phishing and Social Engineering:
- Cybercriminals use deceptive tactics to trick individuals into revealing sensitive information. Phishing involves fraudulent emails, messages, or websites that impersonate legitimate entities to obtain login credentials, financial data, or other personal information.
- Malware Attacks:
- Malicious software, or malware, includes viruses, trojan horses, ransomware, and spyware. Cybercriminals use malware to compromise systems, steal data, or disrupt operations. Ransomware encrypts files, demanding payment for their release.
- Identity Theft:
- Cybercriminals engage in identity theft to steal personal information, such as Social Security numbers or credit card details. This information is often used to commit financial fraud, open unauthorized accounts, or impersonate victims.
- Financial Fraud:
- Online financial fraud includes various schemes, such as credit card fraud, investment scams, and unauthorized fund transfers. Cybercriminals exploit vulnerabilities in online payment systems and banking platforms.
- Distributed Denial of Service (DDoS) Attacks:
- DDoS attacks overwhelm a target’s online services, rendering them unavailable to users. Cybercriminals achieve this by flooding the target’s servers with traffic, disrupting normal operations and causing financial losses.
- Cyber Espionage:
- Nation-states, criminal organizations, or competitors engage in cyber espionage to steal sensitive information, intellectual property, or government secrets. Espionage attacks can have significant geopolitical implications.
- Insider Threats:
- Insider threats involve individuals within an organization exploiting their access to compromise security. This could be for personal gain, revenge, or inadvertently through negligence.
- Online Extortion:
- Cybercriminals may engage in online extortion by threatening to release sensitive information or launch attacks unless a victim pays a ransom. This tactic is prevalent in cases of data breaches.
- Online Harassment and Cyberbullying:
- Individuals may become victims of online harassment, stalking, or cyberbullying. This includes the malicious spread of false information, personal attacks, and intimidation through digital channels.
- IoT-based Attacks:
- Cybercriminals target vulnerabilities in Internet of Things (IoT) devices to compromise networks or launch attacks. This could lead to unauthorized access, data breaches, or disruption of connected devices.
Global Prevalence and Need for Proactive Measures:
Cybercrime is a pervasive and growing global threat. The interconnected nature of the digital world means that cybercriminals can target individuals, businesses, and governments worldwide. The financial impact of cybercrime is staggering, with billions of dollars lost annually.
A proactive stance against digital threats is imperative to mitigate the risks associated with cybercrime. This involves:
- Investment in Cybersecurity:
- Governments, businesses, and individuals must invest in robust cybersecurity measures, including advanced threat detection, encryption, and secure authentication protocols.
- Global Collaboration:
- International collaboration is essential to combat cybercrime effectively. Sharing threat intelligence, coordinating responses, and establishing common cybersecurity standards contribute to a united defense.
- Education and Awareness:
- Public awareness campaigns and educational initiatives are crucial to inform individuals about cyber threats and best practices. Informed users are better equipped to recognize and thwart cybercriminal activities.
- Legislation and Regulation:
- Governments should enact and enforce stringent cybersecurity laws and regulations. These measures provide a legal framework to prosecute cybercriminals and hold organizations accountable for inadequate security practices.
- Continuous Innovation:
- The cybersecurity landscape is dynamic, requiring continuous innovation. Ongoing research and development efforts are necessary to stay ahead of evolving cyber threats and vulnerabilities.
By taking a proactive stance, society can collectively strengthen its resilience against cybercrime, protect sensitive information, and foster a more secure digital environment for all stakeholders.
The Role of Individuals in Cybersecurity
Empowering individuals to take proactive measures for their online security is essential in today’s digital landscape. By adopting responsible practices, individuals can mitigate risks and contribute to creating a safer online environment. Here are key actions individuals can take to enhance their online security:
- Strong and Unique Passwords:
- Create strong, unique passwords for each online account. Use a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information like names or birthdays. Regularly update passwords.
- Enable Multi-Factor Authentication (MFA):
- Enable MFA whenever possible. This adds an extra layer of security by requiring a secondary verification step, such as a code sent to a mobile device, in addition to the password.
- Regularly Update Software and Apps:
- Keep operating systems, software, and applications up-to-date. Updates often include security patches that address vulnerabilities and enhance overall system security.
- Be Cautious with Emails and Links:
- Avoid clicking on links or downloading attachments from unsolicited or suspicious emails. Verify the legitimacy of emails before providing any personal information or clicking on embedded links.
- Educate Yourself on Common Scams:
- Stay informed about common online scams and phishing tactics. Understanding the methods used by cybercriminals makes it easier to recognize and avoid falling victim to fraudulent activities.
- Secure Wi-Fi Networks:
- Use strong, unique passwords for Wi-Fi networks. Employ WPA3 encryption if available, and regularly update router firmware to address security vulnerabilities and protect against unauthorized access.
- Review Privacy Settings:
- Regularly review and adjust privacy settings on social media platforms and other online accounts. Limit the information shared publicly and be mindful of the permissions granted to applications.
- Back Up Important Data:
- Regularly back up important data to an external hard drive or a secure cloud service. In the event of a cyber incident, having backups ensures data recovery.
- Use Reputable Security Software:
- Install and update reputable antivirus and anti-malware software. These programs help detect and remove malicious software, providing an additional layer of defense against online threats.
- Limit Personal Information Sharing:
- Be cautious about sharing personal information online. Avoid oversharing on social media platforms, and only provide necessary information on websites and applications.
- Monitor Financial Statements:
- Regularly review bank and credit card statements for any unauthorized or suspicious transactions. Report discrepancies to financial institutions promptly.
- Secure Your Mobile Devices:
- Set strong passcodes or use biometric authentication on mobile devices. Regularly update software and apps on smartphones and tablets to address security vulnerabilities.
- Educate Yourself on Social Engineering:
- Learn about social engineering tactics, such as pretexting and impersonation. Be skeptical of unsolicited communication and verify the identity of individuals or organizations requesting sensitive information.
- Regularly Check and Update Privacy Policies:
- Stay informed about the privacy policies of websites and online services. Regularly check for updates or changes to these policies and adjust your settings accordingly.
- Participate in Cybersecurity Awareness Programs:
- Engage in cybersecurity awareness programs and campaigns. Many organizations and governments offer resources to educate the public about online threats and best practices.
By adopting these proactive measures, individuals contribute not only to their personal online security but also to the overall safety of the digital environment. Building a culture of responsible online behavior is essential for creating a more secure and resilient online ecosystem for everyone.
Cybersecurity as a Shared Responsibility
The maintenance of a secure online ecosystem is a collective effort that requires collaboration and shared responsibility among individuals, businesses, and governments. Each stakeholder plays a crucial role in strengthening the overall cybersecurity posture. Emphasizing this shared responsibility is vital for creating a safer digital environment. Here’s a deeper exploration of the collaborative efforts needed:
- Individual Responsibility:
- Individuals are the foundation of a secure online ecosystem. They need to adopt good cybersecurity practices, such as using strong passwords, enabling multi-factor authentication, and staying informed about online threats. By taking personal responsibility, individuals contribute to a safer digital space for themselves and others.
- Businesses as Custodians of Data:
- Businesses hold significant responsibility for securing the data they handle. This involves implementing robust cybersecurity measures, regularly updating security protocols, and providing comprehensive training for employees. A commitment to data protection not only safeguards the business but also contributes to a more secure digital ecosystem.
- Government Regulation and Oversight:
- Governments play a crucial role in shaping and enforcing the legal framework for online security. Establishing and enforcing cybersecurity laws, regulations, and standards set the groundwork for businesses and individuals to follow. Governments can also facilitate collaboration and information sharing across sectors.
- Public-Private Collaboration:
- Public-private collaboration is essential for a holistic approach to cybersecurity. Businesses and government agencies should share threat intelligence, collaborate on research and development, and work together to respond to cyber incidents effectively. Such partnerships enhance the collective ability to defend against evolving threats.
- Global Cooperation:
- Cyber threats transcend borders, making global cooperation imperative. Nations must collaborate to address cybersecurity challenges collectively. International agreements, joint initiatives, and shared best practices contribute to a united front against cyber threats and promote global cybersecurity resilience.
- Education and Awareness Campaigns:
- Promoting cybersecurity awareness is a shared responsibility among individuals, businesses, and governments. Educational initiatives, awareness campaigns, and training programs contribute to a better-informed society, reducing the likelihood of falling victim to cyber threats.
- Research and Development Initiatives:
- Collaboration in research and development is crucial for staying ahead of emerging cyber threats. Governments, businesses, and academic institutions should work together to advance cybersecurity technologies, strategies, and policies.
- Incident Response Coordination:
- Collaboration in incident response is vital for minimizing the impact of cyber incidents. Governments, businesses, and individuals should establish communication channels and response protocols to coordinate efforts effectively during security breaches.
- Standardization of Security Practices:
- Standardizing cybersecurity practices across industries and sectors fosters a common understanding of security requirements. Governments, businesses, and industry bodies should collaborate to develop and promote consistent cybersecurity standards.
- Continuous Adaptation to Threats:
- The dynamic nature of cyber threats requires a continuous and adaptive approach to security. Regular collaboration and communication enable stakeholders to adapt quickly to emerging threats and evolving technologies.
- Public Support and Advocacy:
- Individuals, businesses, and governments should advocate for strong cybersecurity measures. Public support for policies that enhance online security encourages adherence to best practices and the development of robust security measures.
- Legislation to Combat Cybercrime:
- Governments must enact and enforce legislation to combat cybercrime. This includes laws that deter malicious activities, prosecute offenders, and protect the rights of individuals and businesses in the digital realm.
By recognizing the shared responsibility and fostering collaboration, individuals, businesses, and governments can collectively build a more secure online ecosystem. Collaboration enhances the capacity to respond to emerging threats, strengthens defenses, and promotes a resilient digital environment for everyone.
Cybersecurity Awareness
Cultivating a cybersecurity-conscious mindset is essential for staying informed about current threats and ensuring a secure digital experience. Here are tips to help individuals develop this mindset and encourage ongoing awareness:
- Stay Informed:
- Regularly read reputable cybersecurity news sources, blogs, and reports to stay updated on the latest threats, vulnerabilities, and security trends. Knowledge is a powerful tool in navigating the ever-evolving landscape of cybersecurity.
- Follow Security Experts:
- Follow cybersecurity experts, organizations, and professionals on social media platforms. Many experts share insights, tips, and real-time updates about emerging threats. Engaging with their content can enhance your understanding of current cybersecurity issues.
- Participate in Webinars and Workshops:
- Attend webinars, workshops, and online courses hosted by cybersecurity professionals. These events often provide in-depth insights into specific threats, preventive measures, and best practices for maintaining digital security.
- Join Online Security Communities:
- Engage with online communities and forums dedicated to cybersecurity discussions. Participating in these communities allows you to share experiences, learn from others, and stay informed about the latest security concerns.
- Subscribe to Security Alerts:
- Subscribe to security alerts and newsletters from reputable cybersecurity organizations. These alerts deliver timely information about new threats, vulnerabilities, and recommended security measures directly to your inbox.
- Conduct Regular Security Audits:
- Periodically review the security settings of your online accounts, devices, and applications. Ensure that you understand the privacy controls available to you and adjust settings based on your preferences and the latest security recommendations.
- Learn from Past Incidents:
- Analyze notable cybersecurity incidents and breaches to understand the tactics used by cybercriminals. Learning from past incidents can provide valuable insights into potential vulnerabilities and help you better protect yourself against similar threats.
- Practice Safe Online Behavior:
- Develop a habit of practicing safe online behavior, such as verifying the authenticity of websites before entering personal information, using secure Wi-Fi connections, and avoiding clicking on suspicious links in emails or messages.
- Regularly Update Software and Devices:
- Enable automatic updates for your operating system, software, and applications. Keeping your software up-to-date ensures that you have the latest security patches to protect against known vulnerabilities.
- Understand Social Engineering Tactics:
- Familiarize yourself with common social engineering tactics, such as phishing and impersonation. Be skeptical of unsolicited communications and verify the identity of individuals or organizations requesting sensitive information.
- Implement Multi-Factor Authentication (MFA):
- Enable multi-factor authentication whenever possible. MFA adds an extra layer of protection by requiring additional verification steps beyond just a password, enhancing the security of your accounts.
- Teach Cybersecurity to Others:
- Share your knowledge of cybersecurity with friends, family, and colleagues. Educating others about online threats and best practices not only helps them stay secure but also reinforces your own understanding of the subject.
- Create a Personal Cybersecurity Plan:
- Develop a personalized cybersecurity plan that outlines your security goals, practices, and response procedures. Having a plan in place makes it easier to implement security measures consistently.
- Be Mindful of Internet of Things (IoT) Devices:
- Securely configure and update IoT devices to minimize the risk of security vulnerabilities. Change default passwords, disable unnecessary features, and stay informed about the security practices of IoT manufacturers.
- Promote a Culture of Cybersecurity:
- Foster a cybersecurity-conscious culture in your workplace, community, or family. Encourage open discussions about cybersecurity, share relevant information, and collaborate on best practices to create a collective awareness of digital security.
By incorporating these tips into your daily digital practices, you can develop a cybersecurity-conscious mindset, stay informed about current threats, and contribute to a safer online environment for yourself and those around you. Regular awareness and proactive measures are vital for maintaining a secure and resilient digital experience.
Building a Foundation for Online Safety
Building a strong foundation in online safety is crucial for navigating the digital realm securely. Here’s an outline of fundamental practices that individuals can adopt to establish a secure online presence and develop a proactive approach to cybersecurity:
1. Use Strong and Unique Passwords:
Create complex passwords that include a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information such as names or birthdays. Additionally, use unique passwords for each online account to prevent a security compromise on one platform from affecting others.
2. Enable Two-Factor Authentication (2FA):
Whenever possible, enable two-factor authentication on your accounts. 2FA adds an extra layer of security by requiring a second form of verification, such as a code sent to your mobile device, in addition to your password.
3. Keep Software and Devices Updated:
Regularly update operating systems, software, and applications to ensure that you have the latest security patches. Cybercriminals often exploit vulnerabilities in outdated software, and staying up-to-date helps protect against known security flaws.
Install and Update Security Software:
- Use reputable antivirus and anti-malware software to provide an additional layer of defense against malicious software. Keep these programs updated to ensure they can identify and mitigate new threats.
- Be Cautious with Emails and Links:
- Exercise caution when receiving emails from unknown or suspicious sources. Avoid clicking on links or downloading attachments from unverified emails, as these could lead to phishing attempts or the installation of malware.
- Secure Your Wi-Fi Network:
- Set a strong password for your Wi-Fi network to prevent unauthorized access. Use WPA3 encryption if available, and regularly update your router’s firmware to patch any security vulnerabilities.
- Practice Safe Browsing Habits:
- Verify the legitimacy of websites before entering personal information or making online purchases. Look for HTTPS in the URL to ensure a secure connection, and use browser extensions, such as ad blockers, to enhance security.
- Review Privacy Settings:
- Regularly review and update privacy settings on social media platforms and other online accounts. Limit the amount of personal information visible to the public and be mindful of the permissions granted to applications.
- Back-Up Your Data Regularly:
- Schedule regular backups of your important data, either to an external hard drive or a secure cloud service. This ensures that you can recover your data in the event of a security incident, such as a ransomware attack.
- Educate Yourself on Online Threats:
- Stay informed about the latest cybersecurity threats and best practices. Understand common tactics used by cybercriminals, such as phishing schemes and social engineering, to better recognize and avoid potential risks.
- Secure Your Mobile Devices:
- Apply security measures to your mobile devices, including setting a strong passcode or using biometric authentication. Install security apps that can help locate, lock, or wipe your device if it’s lost or stolen.
- Monitor Financial Transactions:
- Regularly review your financial statements and transactions for any unauthorized or suspicious activity. Report any discrepancies to your financial institution immediately.
- Limit Sharing of Personal Information:
- Be mindful of the information you share online, including on social media. Avoid oversharing details that could be used by cybercriminals for identity theft or other malicious activities.
- Stay Skeptical of Unsolicited Communications:
- Be cautious of unsolicited phone calls, emails, or messages requesting personal information. Verify the legitimacy of the communication through official channels before providing any sensitive data.
- Create a Digital Estate Plan:
- Plan for the future by creating a digital estate plan that outlines how your online accounts should be managed in the event of incapacitation or death. This includes instructions on how to handle social media accounts, email, and other digital assets.
By consistently implementing these fundamental practices, individuals can establish a strong foundation in online safety, creating a more secure digital presence and reducing the risk of falling victim to cyber threats. Regular awareness and proactive measures are key to maintaining a resilient and secure online environment.